Abuse Reporting: Difference between revisions
→Adding a spam button to MUAs: summarize thread discussion |
No edit summary |
||
| (13 intermediate revisions by 2 users not shown) | |||
| Line 11: | Line 11: | ||
==Abuse Reporting Format (ARF)== | ==Abuse Reporting Format (ARF)== | ||
The format for transmitting abuse reports | The format for transmitting abuse reports is defined in [RFC 5965]. See ''abuse-feedback-report'' list. The IETF is looking at extenstions to it. | ||
<!-- Handy? easier integration with wikipedia is possible by adding a MySQL record, as exemplified in | |||
http://www.mediawiki.org/wiki/Manual:Interwiki#Single_line --> | |||
See also the Wikipedia [http://en.wikipedia.org/wiki/Feedback_Loop_%28email%29 page]. | |||
While it is felt that proper use of abuse | ==The Feedback Loop (FBL) and other usage of abuse reports== | ||
Huge mailbox providers may provide a means for ESPs to get abuse reports issued for messages that had been sent by themselves. This tool can be used to automate opt-out. The sender should tag each message, setting an opaque token and possibly signing it, so as to be able to retrieve necessary submission details. | |||
Another use of abuse reports is to tune an MX server's spam filter. For Bayesian filters this requires a spam/ham indicator. Some hosts automatically convert reports into unsubscribe requests when the reported message contained a ''List-Unsubscribe'' header field. | |||
[[Image:Abuse-report-flow.png|thumb|right|350px|Hypothetical usage of an abuse report (green) submitted in response to a spam message (violet).]] | |||
While it is felt that proper use of abuse reports may result in reliable reputation recording, how abuse reports should be routed is still a debatable question. Rough consensus indicates that users should send abuse reports to their mailbox providers. However, a third party can manage the ''Reporting Service'' instead of (or in addition to) the ''Last MX''. For example, [http://www.spamcop.net/ SpamCop] offers such service. FBLs as operated, e.g., by [http://returnpath.net/ ReturnPath], are not scalable and may be questionable from a privacy point of view. The [http://abusix.org/ Abusix] approach provides for routing abuse reports hierarchically, through top level IP assignments. The image beside depicts possible use: | |||
# Tuning filters at the 1st MX, assuming it is on the ''recipient side''. The 1st MX can be identified as ''responsible for receiving'', e.g. by authentication results. | |||
# Let the spammer's MSA suppress further attempts; this step is useless and questionable if the MSA is directly operated by the spammer. The MSA can be identified as ''responsible for sending'', e.g. by author signatures. | |||
# Arguably, connection providers should terminate contracts with blatantly spamming MSAs. The connection provider can be identified via RIR whois; Abusix's database provides abuse-box lookup by IP address. | |||
# Reputation trackers should verify whether the MSA actually blocks the spammer. | |||
The ''Reputation tracker'', a.k.a. ''vouching service'', sometimes also referred to as ''The "Mythical" Global Reputation System'', would better operations and extend the functionality that is currently obtained by submitting mail through a well-reputed mailbox provider, as it decouples IP addresses from senders' reputation<ref>{{list archive|msg=15884|subject="Mythical" Global Reputation System|from=John Leslie|date=Sun, 20 Dec 2009 18:21:04 -0500}}</ref>. | |||
<br style="clear:both" /> | |||
==Adding a spam button to MUAs== | ==Adding a spam button to MUAs== | ||
Difficulties stem from the fact that a user may have multiple mailbox providers, which rules out single-address configurations<ref name="start">{{list archive|msg=15780|subject=Adding a spam button to MUAs|from=John R. Levine|date=Wed, 9 Dec 2009 00:35:03 -0500}}</ref>. | |||
The possibility that reports are cascaded back to the spammer may be considered a potential hazard that exposes the reporters and allows list washing. However, it has been pointed out that spammers are not interested in feedback and don't bother. There is also concern that a button might cause a flood of unwanted messages, specially when multiple targets can be determined. | The possibility that reports are cascaded back to the spammer may be considered a potential hazard that exposes the reporters and allows list washing<ref name="bobotek">{{list archive|msg=15790||from=BOBOTEK, ALEX (ATTCINW)|date=Tue, 8 Dec 2009 23:08:56 -0800}}</ref>. However, it has been pointed out that spammers are not interested in feedback and don't bother<ref>{{list archive|msg=15802|from=der Mouse|date=Wed, 9 Dec 2009 21:47:12 -0500 (EST)}}</ref>. There is also concern that a button might cause a flood of unwanted messages<ref name="bobotek" />, specially when multiple targets can be determined. | ||
===Message's header based approach=== | ===Message's header based approach=== | ||
An MX server may embed an header field indicating the address where abuse reports may be sent. If the MX doesn't support such field, MUAs may use the field provided by the sender, if any. Otherwise, MX operators may override that by removing the field, or by replacing it with their own FBL reporting address instead. | An MX server may embed an header field indicating the address where abuse reports may be sent. If the MX doesn't support such field, MUAs may use the field provided by the sender, if any. Otherwise, MX operators may override that by removing the field, or by replacing it with their own FBL reporting address instead.<ref>{{list archive|msg=15782|from=Steve Atkins|date=Tue, 8 Dec 2009 22:00:50 -0800}}</ref> | ||
Reusing existing field has also been proposed: the topmost ''Received'', any ''Delivered-To'', ''VBR-Info'', or any trusted ''Authentication-Results''. The latter one already requires users to confirm that they trust the relevant ''authserv-id'', thereby clearing that hazard concern. Fields with multiple values allow for multiple targets, which may be needed for forwarded messages in case abuse reports are used to tune spam filters. In addition, using a DNS RR to store one or more addresses allows even more flexibility: verifying that the service is actually supported, using addresses other than ''abuse@'', and directly sending copies to reputation providers seem valid demands that a DNS call can fulfill. | Reusing existing field has also been proposed: the topmost ''Received''<ref name="bobotek" />, any ''Delivered-To'', ''VBR-Info'', or any trusted ''Authentication-Results''. The latter one already requires users to confirm that they trust the relevant ''authserv-id'', thereby clearing that hazard concern<ref>{{list archive|msg=15786|from=Alessandro Vesely|date=Wed, 09 Dec 2009 12:32:49 +0100}}</ref>. Fields with multiple values allow for multiple targets, which may be needed for forwarded messages in case abuse reports are used to tune spam filters. In addition, using a DNS RR to store one or more addresses allows even more flexibility: verifying that the service is actually supported, using addresses other than ''abuse@'', and directly sending copies to reputation providers seem valid demands that a DNS call can fulfill. | ||
===Client's protocol based approach=== | ===Client's protocol based approach=== | ||
Setting up an IMAP folder for this purpose has the advantage of requiring no special software on clients. This is in facts the most common solution for servers that maintain per-user Bayesian data, although it may be difficult to interpret users' intent in a non-interactive environment, and notwithstanding possible confusion or conflict with junk folders maintained by the client. When the SUBMIT and IMAP servers coincide, sending the report can be optimized by using BURL or similar techniques. | Setting up an IMAP folder for this purpose has the advantage of requiring no special software on clients. This is in facts the most common solution for servers that maintain per-user Bayesian data, although it may be difficult to interpret users' intent in a non-interactive environment, and notwithstanding possible confusion or conflict with junk folders maintained by the client. When the SUBMIT and IMAP servers coincide, sending the report can be optimized by using BURL or similar techniques. | ||
POP clients have no folders, hence they'd need special machinery, such as a new command to upload an abuse report or to retrieve the address where it should be sent. | POP clients have no folders, hence they'd need special machinery, such as a new command to upload an abuse report or to retrieve the address where it should be sent<ref name="start" />. | ||
==UI problems and interpretation of spam reports== | |||
Difficulties with manually submitted reports stem from the scarce reliability that characterizes users and their computing equipments<ref>{{list archive|msg=15848|from=Rich Kulawiec|date=Wed, 16 Dec 2009 07:07:42 -0500}}</ref>. Users error rates have been reported to be around 5~10%<ref>{{list archive|msg=15881|from=Jose-Marcio Martins da Cruz|date=Sun, 20 Dec 2009 13:54:14 +0100}} Cormack, G. V. and Kolcz, A. 2009. [http://plg.uwaterloo.ca/~gvcormac/cormacksigir09-spam.pdf Spam filter evaluation with imprecise ground truth]. In ''Proceedings of the 32nd international ACM SIGIR Conference on Research and Development in information Retrieval'' (Boston, MA, USA, July 19 - 23, 2009). SIGIR '09. ACM, New York, NY, 604-611.</ref><ref>{{list archive|msg=15891|from=Matthias Leisi|date=Mon, 21 Dec 2009 19:24:06 +0100}}</ref>. In addition, users tend to categorize mail incoherently as ''wanted/not-wanted''<ref>{{list archive|msg=15888|from=Jose-Marcio Martins da Cruz|date=Mon, 21 Dec 2009 15:32:41 +0100}}</ref> rather than ''legitimate/abusive'' (never mind the ''ham/spam'' dichotomy, which is fuzzy by definition.) Accordingly, servers may resort to interpret users' intentions by extracting further info from reported messages, e.g., if the sender has sent multiple messages before and it has a List-Unsubscribe: header, it's probably an opt-out, not a spam complaint<ref>{{list archive|msg=15900|from=John Levine|date=23 Dec 2009 01:53:00 -0000}}</ref>. | |||
UI design includes issues such as the number of buttons that users can reach. That UI might be configurable, so as to suit users with different skills<ref>{{list archive|msg=15898|from=Nathaniel Borenstein|date=Tue, 22 Dec 2009 14:54:07 -0500}}</ref>. It seems clear that some experimentation is needed in order to understand users behavior<ref>{{list archive|msg=15894|from=Ian Eiloart|date=Tue, 22 Dec 2009 11:40:24 +0000}}</ref>. However, besides a user's skill and the UI design, a mailbox provider's stance<ref>{{list archive|msg=15899|from=Michael Thomas|date=Tue, 22 Dec 2009 12:56:34 -0800}}</ref> and any effects of the way it processes abuse reports will also play a role. | |||
==See also== | |||
[[Adding a junk button to MUAs]] | |||
==References== | |||
<References /> | |||
Latest revision as of 13:11, 9 November 2011
| Anti-spam technique: Abuse Reporting | |
|---|---|
| Date of first use: | Before 2003 |
| Effectiveness: | ? |
| Popularity: | Medium |
| Difficulty of implementation: | ? |
| Where implemented: | External |
| Harm: | ? |
Abuse Reporting is a cooperative technique whereby spam is suppressed at the origin by the administrators of an MSA. Mail domains' reputation can be preserved by limiting outgoing spam, thus operators are motivated to suppress spamming. Probably the earliest anti-spam defense, this technique relies on end users to submit abuse reports timely and correctly. It is supported by huge mailbox providers, who feature a This is Spam (TiS) button on their web-based mail clients.
Abuse Reporting Format (ARF)
The format for transmitting abuse reports is defined in [RFC 5965]. See abuse-feedback-report list. The IETF is looking at extenstions to it.
See also the Wikipedia page.
The Feedback Loop (FBL) and other usage of abuse reports
Huge mailbox providers may provide a means for ESPs to get abuse reports issued for messages that had been sent by themselves. This tool can be used to automate opt-out. The sender should tag each message, setting an opaque token and possibly signing it, so as to be able to retrieve necessary submission details.
Another use of abuse reports is to tune an MX server's spam filter. For Bayesian filters this requires a spam/ham indicator. Some hosts automatically convert reports into unsubscribe requests when the reported message contained a List-Unsubscribe header field.
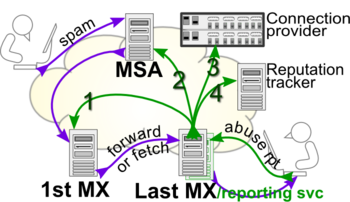
While it is felt that proper use of abuse reports may result in reliable reputation recording, how abuse reports should be routed is still a debatable question. Rough consensus indicates that users should send abuse reports to their mailbox providers. However, a third party can manage the Reporting Service instead of (or in addition to) the Last MX. For example, SpamCop offers such service. FBLs as operated, e.g., by ReturnPath, are not scalable and may be questionable from a privacy point of view. The Abusix approach provides for routing abuse reports hierarchically, through top level IP assignments. The image beside depicts possible use:
- Tuning filters at the 1st MX, assuming it is on the recipient side. The 1st MX can be identified as responsible for receiving, e.g. by authentication results.
- Let the spammer's MSA suppress further attempts; this step is useless and questionable if the MSA is directly operated by the spammer. The MSA can be identified as responsible for sending, e.g. by author signatures.
- Arguably, connection providers should terminate contracts with blatantly spamming MSAs. The connection provider can be identified via RIR whois; Abusix's database provides abuse-box lookup by IP address.
- Reputation trackers should verify whether the MSA actually blocks the spammer.
The Reputation tracker, a.k.a. vouching service, sometimes also referred to as The "Mythical" Global Reputation System, would better operations and extend the functionality that is currently obtained by submitting mail through a well-reputed mailbox provider, as it decouples IP addresses from senders' reputation[1].
Adding a spam button to MUAs
Difficulties stem from the fact that a user may have multiple mailbox providers, which rules out single-address configurations[2].
The possibility that reports are cascaded back to the spammer may be considered a potential hazard that exposes the reporters and allows list washing[3]. However, it has been pointed out that spammers are not interested in feedback and don't bother[4]. There is also concern that a button might cause a flood of unwanted messages[3], specially when multiple targets can be determined.
Message's header based approach
An MX server may embed an header field indicating the address where abuse reports may be sent. If the MX doesn't support such field, MUAs may use the field provided by the sender, if any. Otherwise, MX operators may override that by removing the field, or by replacing it with their own FBL reporting address instead.[5]
Reusing existing field has also been proposed: the topmost Received[3], any Delivered-To, VBR-Info, or any trusted Authentication-Results. The latter one already requires users to confirm that they trust the relevant authserv-id, thereby clearing that hazard concern[6]. Fields with multiple values allow for multiple targets, which may be needed for forwarded messages in case abuse reports are used to tune spam filters. In addition, using a DNS RR to store one or more addresses allows even more flexibility: verifying that the service is actually supported, using addresses other than abuse@, and directly sending copies to reputation providers seem valid demands that a DNS call can fulfill.
Client's protocol based approach
Setting up an IMAP folder for this purpose has the advantage of requiring no special software on clients. This is in facts the most common solution for servers that maintain per-user Bayesian data, although it may be difficult to interpret users' intent in a non-interactive environment, and notwithstanding possible confusion or conflict with junk folders maintained by the client. When the SUBMIT and IMAP servers coincide, sending the report can be optimized by using BURL or similar techniques.
POP clients have no folders, hence they'd need special machinery, such as a new command to upload an abuse report or to retrieve the address where it should be sent[2].
UI problems and interpretation of spam reports
Difficulties with manually submitted reports stem from the scarce reliability that characterizes users and their computing equipments[7]. Users error rates have been reported to be around 5~10%[8][9]. In addition, users tend to categorize mail incoherently as wanted/not-wanted[10] rather than legitimate/abusive (never mind the ham/spam dichotomy, which is fuzzy by definition.) Accordingly, servers may resort to interpret users' intentions by extracting further info from reported messages, e.g., if the sender has sent multiple messages before and it has a List-Unsubscribe: header, it's probably an opt-out, not a spam complaint[11].
UI design includes issues such as the number of buttons that users can reach. That UI might be configurable, so as to suit users with different skills[12]. It seems clear that some experimentation is needed in order to understand users behavior[13]. However, besides a user's skill and the UI design, a mailbox provider's stance[14] and any effects of the way it processes abuse reports will also play a role.
See also
References
- ↑
John Leslie "Mythical" Global Reputation System Sun, 20 Dec 2009 18:21:04 -0500.
- ↑ 2.0 2.1
John R. Levine Adding a spam button to MUAs Wed, 9 Dec 2009 00:35:03 -0500.
- ↑ 3.0 3.1 3.2
BOBOTEK, ALEX (ATTCINW) Re:... Tue, 8 Dec 2009 23:08:56 -0800.
- ↑
der Mouse Re:... Wed, 9 Dec 2009 21:47:12 -0500 (EST).
- ↑
Steve Atkins Re:... Tue, 8 Dec 2009 22:00:50 -0800.
- ↑
Alessandro Vesely Re:... Wed, 09 Dec 2009 12:32:49 +0100.
- ↑
Rich Kulawiec Re:... Wed, 16 Dec 2009 07:07:42 -0500.
- ↑
Jose-Marcio Martins da Cruz Re:... Sun, 20 Dec 2009 13:54:14 +0100.
Cormack, G. V. and Kolcz, A. 2009. Spam filter evaluation with imprecise ground truth. In Proceedings of the 32nd international ACM SIGIR Conference on Research and Development in information Retrieval (Boston, MA, USA, July 19 - 23, 2009). SIGIR '09. ACM, New York, NY, 604-611. - ↑
Matthias Leisi Re:... Mon, 21 Dec 2009 19:24:06 +0100.
- ↑
Jose-Marcio Martins da Cruz Re:... Mon, 21 Dec 2009 15:32:41 +0100.
- ↑
John Levine Re:... 23 Dec 2009 01:53:00 -0000.
- ↑
Nathaniel Borenstein Re:... Tue, 22 Dec 2009 14:54:07 -0500.
- ↑
Ian Eiloart Re:... Tue, 22 Dec 2009 11:40:24 +0000.
- ↑
Michael Thomas Re:... Tue, 22 Dec 2009 12:56:34 -0800.